 | ||
A Wi-Fi deauthentication attack is a type of denial-of-service attack that targets communication between a user and a Wi-Fi wireless access point.
Contents
Technical details
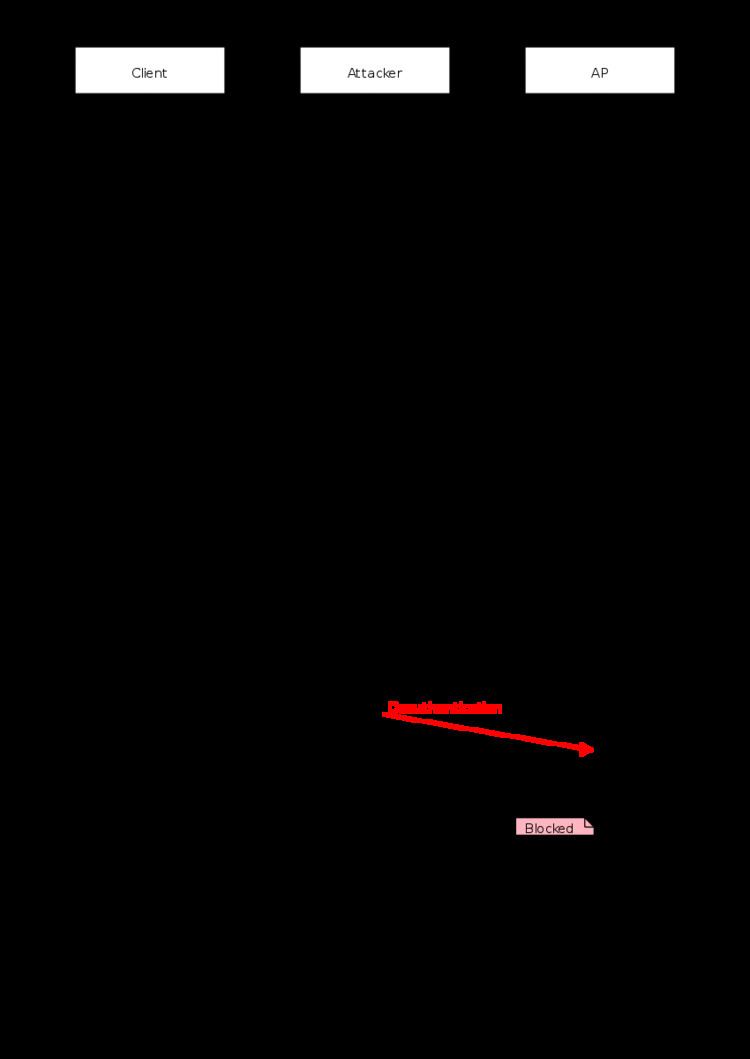
The IEEE 802.11 (Wi-Fi) protocol contains the provision for a deauthentication frame. Sending the frame from the access point to a station is called a "sanctioned technique to inform a rogue station that they have been disconnected from the network".
An attacker can send a wireless access point a deauthentication frame at any time, with a spoofed address for the victim. The protocol does not require any encryption for this frame, even when the session was established with Wired Equivalent Privacy (WEP) for data privacy, and the attacker only needs to know the victim's MAC address, which is available in the clear through wireless network sniffing.
Attacks on hotel guests and convention attendees
The Federal Communications Commission has fined hotels and other companies for launching deauthentication attacks on their own guests; the purpose being to drive them off their own personal hotspots and force them to pay for on-site Wi-Fi services.
Use in password attacks
In order to mount a brute-force or dictionary based WPA password cracking attack on a WiFi user with WPA or WPA2 enabled, a hacker must first sniff the WPA 4-way handshake. The user can be elicited to provide this sequence by first forcing them offline with the deauthentication attack.
In a similar phishing style attack without password cracking, Wifiphisher starts with a deauthentication attack to disconnect the user from his legitimate base station, then mounts a man-in-the-middle attack to collect passwords supplied by an unwitting user.
Toolsets
Aircrack-ng suite, MDK3, Void11, Scapy, and Zulu software can mount a WiFi deauthentication attack. A one-line aircrack-ng command has been published which can do so. The off-the-shelf WiFi Pineapple rogue access point hardware can issue a deauth attack. An open-source project called wifijammer can also automatically scan for and jam all networks within range of an operator.
