Original author(s) | Development status Active Operating system | |
 | ||
Stable release 4.3.0 / July 19, 2016 (2016-07-19) | ||
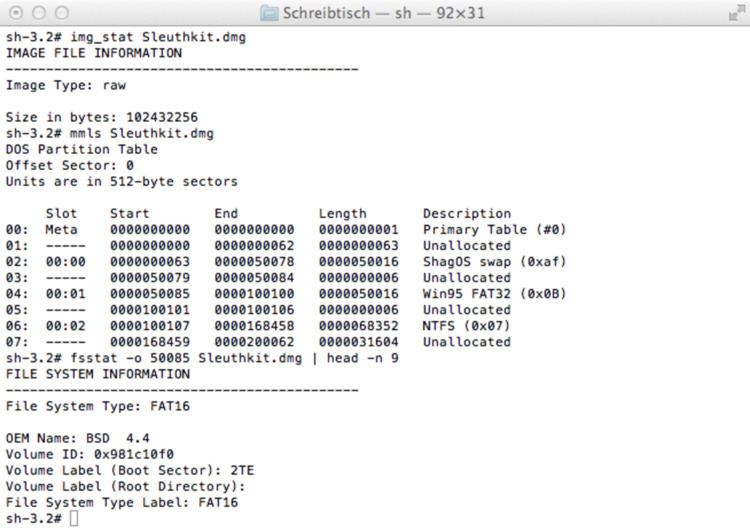
The Sleuth Kit (TSK) is a library and collection of Unix- and Windows-based utilities to facilitate the forensic analysis of computer systems. It was written and is maintained primarily by digital investigator Brian Carrier.
The Sleuth Kit is capable of parsing NTFS, FAT/ExFAT, UFS 1/2, Ext2, Ext3, Ext4, HFS, ISO 9660 and YAFFS2 file systems either separately or within disk images stored in raw (dd), Expert Witness or AFF formats. The Sleuth Kit can be used to examine most Microsoft Windows, most Apple Macintosh OSX, many Linux and some other UNIX computers.
The Sleuth Kit can be used:
The Sleuth Kit is a free, open source suite that provides a large number of specialized command-line based utilities.
It is based on The Coroner's Toolkit, and is the official successor platform.
Tools
Some of the tools included in The Sleuth Kit include:
