 | ||
The slide attack is a form of cryptanalysis designed to deal with the prevailing idea that even weak ciphers can become very strong by increasing the number of rounds, which can ward off a differential attack. The slide attack works in such a way as to make the number of rounds in a cipher irrelevant. Rather than looking at the data-randomizing aspects of the block cipher, the slide attack works by analyzing the key schedule and exploiting weaknesses in it to break the cipher. The most common one is the keys repeating in a cyclic manner.
The attack was first described by David Wagner and Alex Biryukov. Bruce Schneier first suggested the term slide attack to them, and they used it in their 1999 paper describing the attack.
The only requirements for a slide attack to work on a cipher is that it can be broken down into multiple rounds of an identical F function. This probably means that it has a cyclic key schedule. The F function must be vulnerable to a known-plaintext attack. The slide attack is closely related to the related-key attack.
The idea of the slide attack has roots in a paper published by Edna Grossman and Bryant Tuckerman in an IBM Technical Report in 1977. Grossman and Tuckerman demonstrated the attack on a weak block cipher named New Data Seal (NDS). The attack relied on the fact that the cipher has identical subkeys in each round, so the cipher had a cyclic key schedule with a cycle of only one key, which makes it an early version of the slide attack. A summary of the report, including a description of the NDS block cipher and the attack, is given in Cipher Systems (Beker & Piper, 1982).
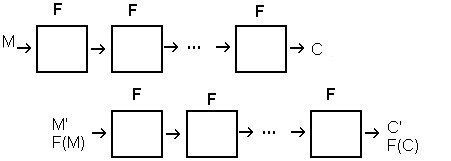
The actual attack
First, to introduce some notation. In this section assume the cipher takes n bit blocks and has a key-schedule using
The slide attack works by breaking the cipher up into identical permutation functions, F. This F function may consist of more than one round of the cipher; it is defined by the key-schedule. For example, if a cipher uses an alternating key schedule where it switches between a
The next step is to collect
The process of finding a slid pair is somewhat different for each cipher but follows the same basic scheme. One uses the fact that it is relatively easy to extract the key from just one iteration of F. Choose any pair of plaintext-ciphertext pairs,
With
Sometimes the structure of the cipher greatly reduces the number of plaintext-ciphertext pairs needed, and thus also a large amount of the work. The clearest of these examples is the Feistel cipher using a cyclic key schedule. The reason for this is given a
