 | ||
Body Area Networks (BANs) constantly interact with their physical environment with the help of sensors. Sensors collect process as well as communicate information gathered from their environment. Thus BANs are inherently cyber-physical systems. The BAN interacts with its physical world (human body) by collecting, processing, and communicating health data (vital signals, temperature, pressure) from the person. This information from the environment that is already being collected can be used to provide security to the BAN. Physiological Value based Security (PVS) uses the vital signals of the human body that is collected during health monitoring operation to provide usable security to BAN.
Contents
Properties of PVS
For PVS to succeed the scheme developed should have the following properties:
- The keys provided by PVS for security are long and random (a basic requirement in any security protocol).
- Knowing the physiological signals at any time will not provide significant advantage in knowing the keys agreed upon in future executions of the scheme, i.e. time variance (required to prevent attacker from guessing future feature values from present ones).
- The physiological stimuli used for PVS is universally (ensures that sensors at different location can measure the same signal).
- Knowing the physiological value of one individual will not provide significant advantage in guessing the keys being agreed by sensors on another individual, i.e. distinctiveness.
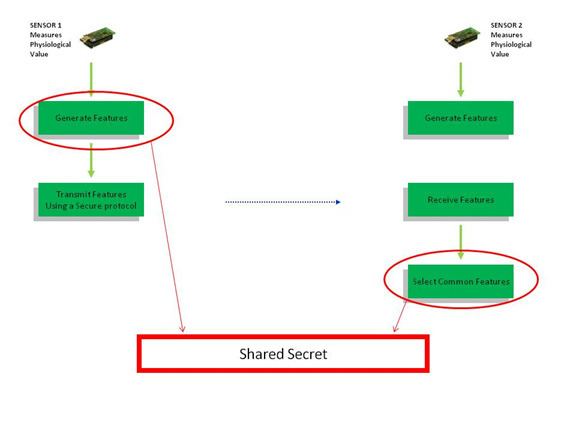
Implementation of PVS using Photoplethysmogram (PPG) signals
Plethysmogram based Key Agreement protocol (PKA) uses PPG signals to provide PVS infrastructure to the BAN. It provides secure key agreement between two sensors that wish to communicate in a BAN.
PKA has been divided into four basic steps as described in Figure 1:
