Used for computer secutity, IODEF (Incident Object Description Exchange Format) is a data format which is used to describe computer security information for the purpose of exchange between Computer Security Incident Response Teams (CSIRTs).
IODEF messages are organized in a human-readable way, and not a machine format. Details of the format are described in RFC 5070. This RFC presents an implementation of the data model in XML as well as the associated DTD.
One of the main characteristics of IODEF is its compatibility with the IDMEF Intrusion Detection Message Exchange Format developed for intrusion detection systems. For this reason, IODEF is heavily based on IDMEF and provides backward compatibility with it.
IODEF is an object-oriented structured format, composed of 47 classes in the first version. The IODEF and IDMEF formats having a lot in common: the field structure is similar to the IDMEF one and it is an extensible format: in addition to the usual Additional Data Class, which allow adding any information relevant to the IODEF message, most enumerations are provided with an "ext" field. This field is used when none of the proposed choices are fitting.
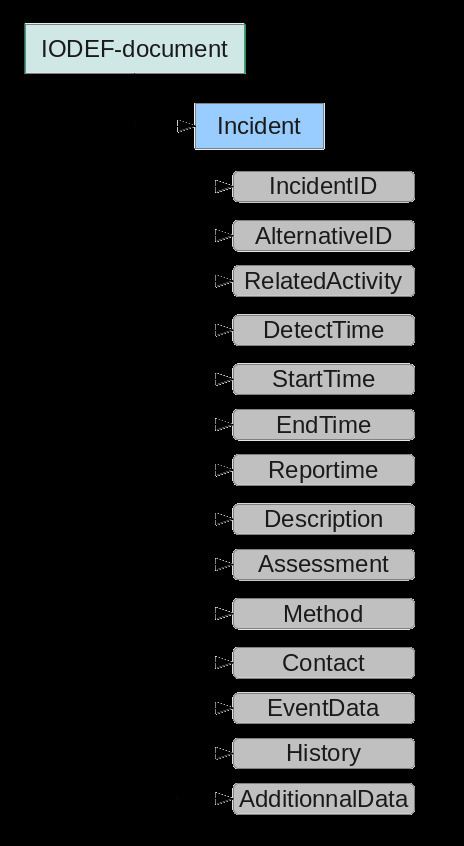
Here is a list of the main fields:
IncidentID : One. An incident identification number assigned to this incident by the CSIRT who creates the IODEF document.AlternativeID : Zero or one. The incidents ID numbers used by other CSIRTs to refer to the incident described in the document.RelatedActivity : Zero or one. The ID numbers of the incidents linked to the one described in this document.DetectTime : Zero or one. Time at which the incident was detected for the first time.StartTime : Zero or one. Time at which the incident started.EndTime : Zero or one. Time at which the incident ended.ReportTime : One. Time at which the incident was reported.Description : Zero or more. ML_STRING. A non-formatted textual description of the event.Assessment : One or more. A characterization of the incident impact.Method : Zero or more. Technics used by the intruder during the incident.Contact : One or more. Contact information for the groups involved in the incident.EventData : Zero or more. Description of the events involving the incident.History : Zero or more. A log, of the events or the notable actions which took place during the incident management.AdditionalData : Zero or more. Mechanism which extends the data model.Below, you can find an example of an IODEF document:
Prelude SIEMIODEFLIB : Python library to create, parse and edit cyber incident reports using the IODEF XML format (RFC 5070)RT-IODEF : Perl module for translating RT tickets to IODEF messages and also maps IODEF to RT’s Custom Fields based on their description tagMantis IODEF Importer : An IODEF (v1.0) importer for the Mantis Cyber Threat Intelligence Mgmt. FrameworkArcSight-IODEF-Perl : A perl module to convert arcsight xml to a standardized iodef messageIODEF ImplementationsIODEF DBIIODEF Pb : This library maps IODEF (RFC 5070) to the google protocol buffer serialization library.XML :: IODEF – A perl module for easily creating/parsing IODEF DocumentsStix output formatter for : Iodef::Pb::SimpleLibrary for parsing IODEF in PHP