 | ||
BORO (Business Objects Reference Ontology) is an approach to developing ontological or semantic models for large complex operational applications that consists of a top ontology as well as a process for constructing the ontology. It was originally developed as a method for mining ontologies from multiple legacy systems – as the first stage in an architectural transformation or software modernization. It has also been used to enable semantic interoperability between legacy systems. It is described in detail in (Partridge 1996, 2005). It is the analysis method used in the development and maintenance of the U.S. Department of Defense Architecture Framework (DoDAF) Meta Model (DM2), where a data modeling working group of over 350 members was able to systematically resolve a broad spectrum of knowledge representation issues.
Contents
History
The method was developed in the late 80's and early 90's by a team of KPMG consultants led by Chris Partridge. The team was working on a complex legacy systems re-engineering project and needed a new approach. The prime challenge of the re-engineering work was to clarify the underlying ontology of the systems and the work focussed on developing a process for mining ontologies and a top ontology that formed the foundation for the analysis. The top ontology was tailored to meet the needs of the re-engineering. Early work established that a key factor was to make a series of clear metaphysical choices to provide a solid (metaphysical) foundation.
A key choice was for an extensional (and hence, four-dimensional) ontology which provided neat criteria of identity. Using this top ontology as a basis, a systematic process for re-engineering legacy systems was developed. From a software engineering perspective, a key feature of this process was the identification of common general patterns, under which the legacy system was subsumed. It has been substantially developed since then.
Much of the method and the associated tools is proprietary, but some aspects have been delivered to the public domain and elements of it have appeared in a number of standards. For example, the ISO standard, ISO 15926 – Industrial automation systems and integration – was heavily influenced by an early version. The IDEAS (International Defence Enterprise Architecture Specification for exchange) standard is based upon BORO, which in turn was used to develop DODAF 2.0. From 2003 to 2008, the start-up company 42 Objects, funded by private equity company 3i worked on developing systems based upon BORO.
Description
The BORO method is designed to be a simple, repeatable process for developing formal ontologies. The method takes an extensional approach to ontology development. The method aims to be grounded in physical reality so that if followed to the letter the method should consistently produce the same ontology given the same inputs. It can then be used for comparing multiple data-sources for semantic matches/mismatches and for re-engineering multiple legacy systems into a coherent whole (either as a new monolithic system, or as a method for designing federation of existing systems).
BORO's purpose is to improve the quality of information and information models, to integrate multiple information sources and extract hidden semantics. The purpose of the method is to re-engineer disparate data sources into a common model. It is meant to be focused on semantic analysis – establishing whether two concepts are the same, if they overlap, or if they are unrelated. This is based on using resources from higher order logic, mathematics and philosophy.
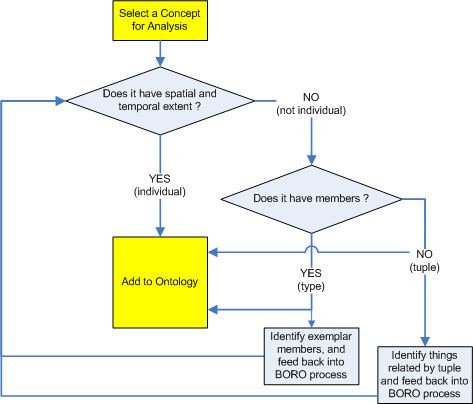
For example in the case of Criterion of identity, the method adopts an extensional approach. As an example, take “Waterloo Bridge” as a term. The first thing we ask is “does it refer to an object that has a spatial and temporal extent ?”. It has spatial extent; it spans the River Thames. However, when we examine the temporal extent we realise there have been two bridges at that site. The first, built in 1817 (two years after the battle of Waterloo) was demolished in 1920. The bridge that stands there now was built in 1942. This analysis has immediately highlighted a problem with a name-based approach – there are two bridges of that name, which one are we referring to? At this point, the analyst can add one or both of the bridges to the ontology, then apply the appropriate names to each.
The process also works for types of things. Take “bridges” as a concept. It doesn’t have spatiotemporal extent, so we go to the next question “does it have members ?”. It does – the members are all the bridges in the world. We then identify some exemplar members – e.g. Waterloo Bridge. At this stage, it is advisable to identify exemplars that are “on the edge” of the set – e.g. things that may or may not be bridges – e.g. pontoons, bridging vehicles, etc. so as to accurately identify the extent of the type.
The final concept covered by the process is the tuple. A tuple is a relationship between things. If the concept under analysis is neither a type nor an individual, then it must be a tuple. We identify the things at the end of the tuple then add it to the ontology.
Traditional methods of data analysis tend to be linguistic; comparison of concepts is based on the names these concepts have. More modern methods have introduced a semantic approach, where the analyst will tend to analyse the underlying senses of the word (meaning). A lot of it depends on the analyst’s domain knowledge and linguistic interpretation. Although BORO produces an ontology (information science) in the very strictest sense of the term, it is not intended to produce the type of ontology (information science) that computer scientists would use for reasoning and inference. BORO is different to many other data analysis techniques in that treats the names of things as a secondary concern. With BORO, the analyst is forced to identify individual concepts by their extent.
The BORO methodology is best summarised as a flowchart:
Presentations
The method has been presented several times, including a tutorial at the Integrated Enterprise Architecture Conference in London in 2008. It was also presented at the UK Ministry of Defence's EKIG conference in October 2009.
